1-Click iPhone and Android Exploits Target Tibetan Users via WhatsApp
 A team of Canadian cybersecurity researchers has uncovered a sophisticated and targeted mobile hacking campaign that is targeting high-profile members of various Tibetan groups with one-click exploits for iOS and Android devices.
A team of Canadian cybersecurity researchers has uncovered a sophisticated and targeted mobile hacking campaign that is targeting high-profile members of various Tibetan groups with one-click exploits for iOS and Android devices.
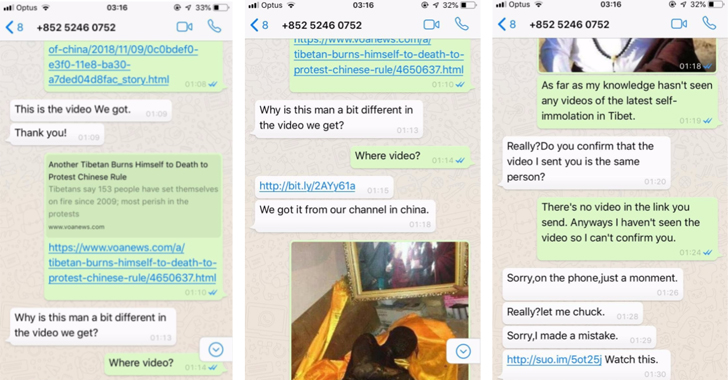
Dubbed Poison Carp by University of Toronto's Citizen Lab, the hacking group behind this campaign sent tailored malicious web links to its targets over WhatsApp, which, when opened, exploited web browser and privilege escalation vulnerabilities to install spyware on iOS and Android devices stealthily.
"Between November 2018 and May 2019, senior members of Tibetan groups received malicious links in individually tailored WhatsApp text exchanges with operators posing as NGO workers, journalists, and other fake personas," the researchers say.
What's more? The researchers said they found "technical overlaps" of Poison Carp with two recently discovered campaigns against the Uyghur community in China—the iPhone hacking campaign reported by experts at Google and the Evil Eye campaign published by Volexity last month.
Based on the similarities of the three campaigns, researchers believed that the Chinese government sponsors Poison Carp group.
Poison Carp campaign exploits a total of 8 distinct Android browser exploits to install a previously undocumented fully-featured Android spyware, called MOONSHINE and one iOS exploit chain to stealthily install iOS spyware on 'users' device—none of which were zero days.
tibet malware attack
"Four of the MOONSHINE exploits are clearly copied from working exploit code posted by security researchers on bug trackers or GitHub pages," the report says.
Researchers observed a total of 17 intrusion attempts against Tibetan targets that were made over that period, 12 of which contained links to the iOS exploit.
Once installed, the malicious implant allows attackers to:
gain full control of victims device,
exfiltrate data including text messages, contacts, call logs, and location data,
access the 'device's camera and microphone,
exfiltrate private data from Viber, Telegram, Gmail, Twitter, and WhatsApp,
downloads and install additional malicious plugins.
Besides this, researchers also observed a malicious OAuth application that the same group of attackers used to gain access to its 'victims' Gmail accounts by redirecting them to a decoy page designed to convince them that the app served a legitimate purpose.
Among the victims that were targeted by the Poison Carp hackers between November 2018 and May 2019 include the Private Office of Tibetan Buddhist leader the Dalai Lama, the Central Tibetan Administration, the Tibetan Parliament, Tibetan human rights groups, and individuals holding senior positions in their respective organizations.
Though this is not the first case attempting to target Tibetan government, the researchers say the new Poison Carp campaign is "the first documented case of one-click mobile exploits used to target Tibetan groups."
"It represents a significant escalation in social engineering tactics and technical sophistication compared to what we typically have observed being used against the Tibetan community," the report reads.
After the disclosure of iPhone hacking campaign, Apple released a statement last month confirming that the iOS campaign targeted the Uyghur community and saying that the company patched the vulnerabilities in question in February this year.
Since none of the iOS and Android vulnerabilities exploited in the campaign is zero-day, users are highly recommended always to keep their mobile devices up-to-date to avoid falling victim to such attacks.
 A team of Canadian cybersecurity researchers has uncovered a sophisticated and targeted mobile hacking campaign that is targeting high-profile members of various Tibetan groups with one-click exploits for iOS and Android devices.
A team of Canadian cybersecurity researchers has uncovered a sophisticated and targeted mobile hacking campaign that is targeting high-profile members of various Tibetan groups with one-click exploits for iOS and Android devices.Dubbed Poison Carp by University of Toronto's Citizen Lab, the hacking group behind this campaign sent tailored malicious web links to its targets over WhatsApp, which, when opened, exploited web browser and privilege escalation vulnerabilities to install spyware on iOS and Android devices stealthily.
"Between November 2018 and May 2019, senior members of Tibetan groups received malicious links in individually tailored WhatsApp text exchanges with operators posing as NGO workers, journalists, and other fake personas," the researchers say.
What's more? The researchers said they found "technical overlaps" of Poison Carp with two recently discovered campaigns against the Uyghur community in China—the iPhone hacking campaign reported by experts at Google and the Evil Eye campaign published by Volexity last month.
Based on the similarities of the three campaigns, researchers believed that the Chinese government sponsors Poison Carp group.
Poison Carp campaign exploits a total of 8 distinct Android browser exploits to install a previously undocumented fully-featured Android spyware, called MOONSHINE and one iOS exploit chain to stealthily install iOS spyware on 'users' device—none of which were zero days.
tibet malware attack
"Four of the MOONSHINE exploits are clearly copied from working exploit code posted by security researchers on bug trackers or GitHub pages," the report says.
Researchers observed a total of 17 intrusion attempts against Tibetan targets that were made over that period, 12 of which contained links to the iOS exploit.
Once installed, the malicious implant allows attackers to:
gain full control of victims device,
exfiltrate data including text messages, contacts, call logs, and location data,
access the 'device's camera and microphone,
exfiltrate private data from Viber, Telegram, Gmail, Twitter, and WhatsApp,
downloads and install additional malicious plugins.
Besides this, researchers also observed a malicious OAuth application that the same group of attackers used to gain access to its 'victims' Gmail accounts by redirecting them to a decoy page designed to convince them that the app served a legitimate purpose.
Among the victims that were targeted by the Poison Carp hackers between November 2018 and May 2019 include the Private Office of Tibetan Buddhist leader the Dalai Lama, the Central Tibetan Administration, the Tibetan Parliament, Tibetan human rights groups, and individuals holding senior positions in their respective organizations.
Though this is not the first case attempting to target Tibetan government, the researchers say the new Poison Carp campaign is "the first documented case of one-click mobile exploits used to target Tibetan groups."
"It represents a significant escalation in social engineering tactics and technical sophistication compared to what we typically have observed being used against the Tibetan community," the report reads.
After the disclosure of iPhone hacking campaign, Apple released a statement last month confirming that the iOS campaign targeted the Uyghur community and saying that the company patched the vulnerabilities in question in February this year.
Since none of the iOS and Android vulnerabilities exploited in the campaign is zero-day, users are highly recommended always to keep their mobile devices up-to-date to avoid falling victim to such attacks.
Comments