What an Apple phishing attack looks like
Watch an Apple phishing attack from start to finish, including a look at what the criminals see and the code that drives these types of scams.
How can you tell the difference between a legitimate email and a phishing attack? Host Steve Ragan shows what an Apple phishing attack looks like, screen by screen, showing the difference between the real and the fake.
Today's top stories
- 11 ways to hack 2FA
- 8 hot cyber security trends (and 4...
- How to write an information security...
- 5 top machine learning use cases for...
- GuardiCore Centra provides visibility,...
Today on Salted Hash, we’re going to look at a phishing attack from two sides. The first side will be what the victim sees. After that, we're going to see what the criminal sees. We'll also discuss some steps administrators can take to uncover
What I've done is recorded a screencast (SC 01) and walked through the attack and the phishing kit itself. This is the first take, but I plan on doing others. So please forgive any slight errors. Eventually, I'd like to get to a point where I can demonstrate live attacks and tailor these videos to people both inside and outside of the echo chamber.
So, with that said, enjoy!
Email:
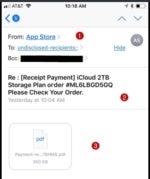
The Apple phishing attack in the video starts with an email (thanks to @Mrs_Bonds2015 for sharing this with us on Twitter). The message is designed to pique the victim's curiosity. It does this by informing them about a purchase and providing a PDF file that's a receipt (2). Most users will wonder what's happening, but others might panic some and wonder who just ripped them off for $50.00.
However, there are a few things that stand out here. First the email is addressed to "undisclosed-recipients" and has a single address in the BCC field (1). So, ask yourself, why are these people getting a copy of your receipt? These are pretty obvious red flags, but the concern about losing money will cause some to ignore the general rule about random email attachments and open the PDF file anyway (3).
Opening the PDF:
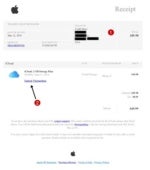
When the PDF is opened, the invoice displayed looks legitimate. There are some basic connections to the email via Order ID (1) and a product description related to what was mentioned in the email subject (2). What the criminal is hoping for is a bit of panic and a click to the Cancel Order link. However, clicking on any of the links in the PDF will forward you to the phishing kit, which powers the phishing attack.
A clever phishing attack against Apple:
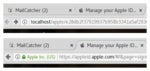
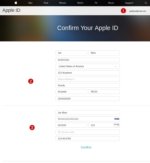
At first glance (see the image to the left) the phishing portal looks almost exactly like the real Apple login screen. But there are a few things that standout. For example, look at the URL bar. It's missing Extended Validation. In fact, it doesn't even have HTTPS enabled. When this kit was hosted on a live server (here it's hosted in Salted Hash's lab), it was missing HTTPS there as well.
The form itself is also a red flag, as Apple doesn't require passwords on the main page. You'll enter your username first, then on the next screen enter your password. Here, the phishing page is asking for both, because the moment you submit credentials, they're compromised.
The page that comes after this login box asks for additional information including name, address, phone number, and date of birth(1). This is followed by a second section (2) requesting credit card details, as well as Social Security Number, if you identify your country as United States of America.
Once again, completing this form and pressing submit will compromise these details and send them over to the criminal.
After all of that, you're forwarded over to the actual Apple.com website, but by this point your Apple ID is in the hands of a crook.
Check out the end of the video if you want to see some of the technical aspects of this kit. Thanks for watching, and remember this was an experiment, so please share some feedback via email or on Twitter.

Comments