Review: Protecting clouds with Cloud Defender from Alert Logic
Cloud Defender is a user-friendly tool that lets local IT staff inspect their cloud deployments to look for evidence of hidden threats or breaches. But it can also be used in a SaaS model, with the cybersecurity team at Alert Logic taking over most cloud-based cybersecurity functions.
Compared to traditional server and client architectures, cloud computing is the new kid on the block. And while cybersecurity best practices are similar within a cloud environment, many of the vulnerabilities and specific threats that target the cloud are different. As such, even organizations with deep cybersecurity teams may need a little help when moving large chunks of their computing infrastructure to the cloud.
That is the idea behind Cloud Defender from Alert Logic. Designed from the ground up as a way to provide protection to web applications, critical data and everything else running or stored within an organization’s cloud, there is a whole sliding scale of support available. At the low end, Cloud Defender is a user-friendly tool that would enable local IT staff to inspect their cloud deployments to look for evidence of hidden threats or breaches. At the other extreme, the 200-person cybersecurity team at Alert Logic can take over most cloud-based cybersecurity functions, offering monitoring, advising and logging of events in a software as a service (SaaS) model. When used as SaaS, Alert Logic will do everything short of remediating problems.
Most organizations are probably going to want to use Cloud Defender as some combination of both SaaS security and as a tool to aid their local teams. The platform is configured for this, making all logs and information collected by the program available for at least a year to local IT staffers.
Cloud Defender works with any cloud environment, including Amazon Web Services (AWS), Microsoft Azure, Google Cloud Services, VMware and others. The test environment for this review was an AWS deployment. There is no difference in pricing based on the cloud environment. Pricing is totally based on the number of nodes being protected and the size of the logfiles being analyzed.
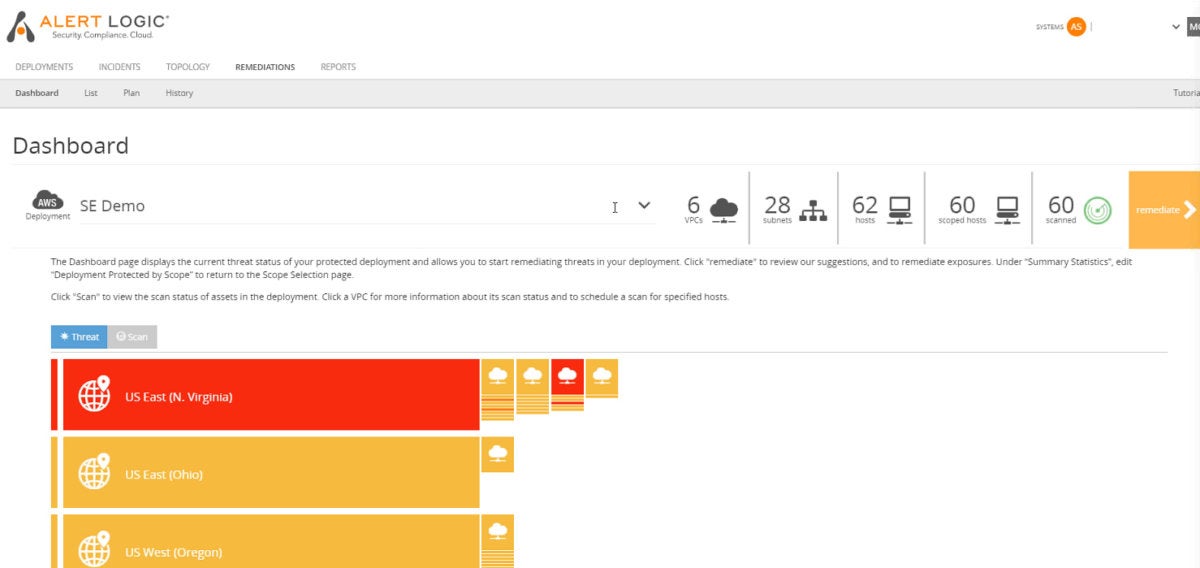
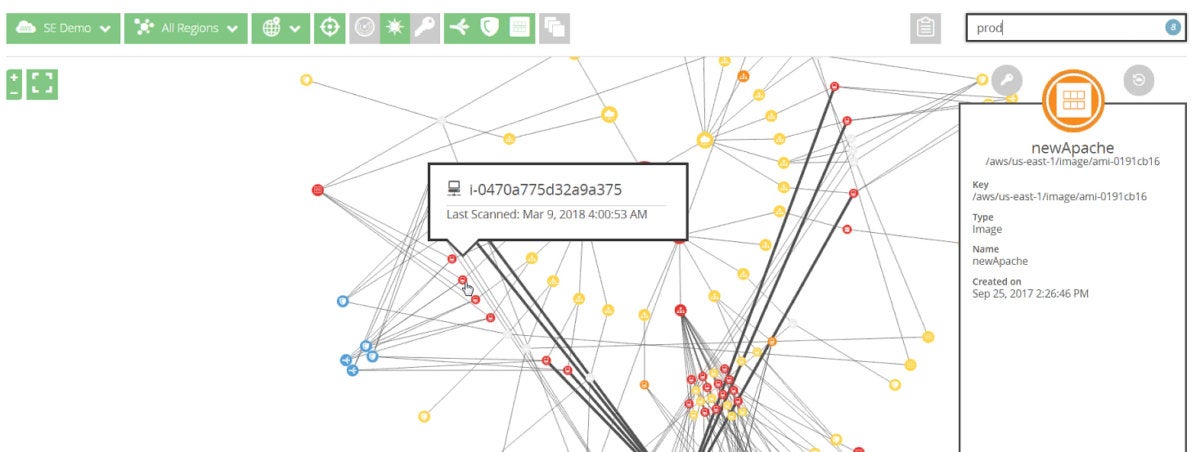
When first installed, Cloud Defender begins discovering cloud assets right away. Even with a massive cloud, the discovery process should take less than an hour. Our test network was mapped in under 15 minutes.
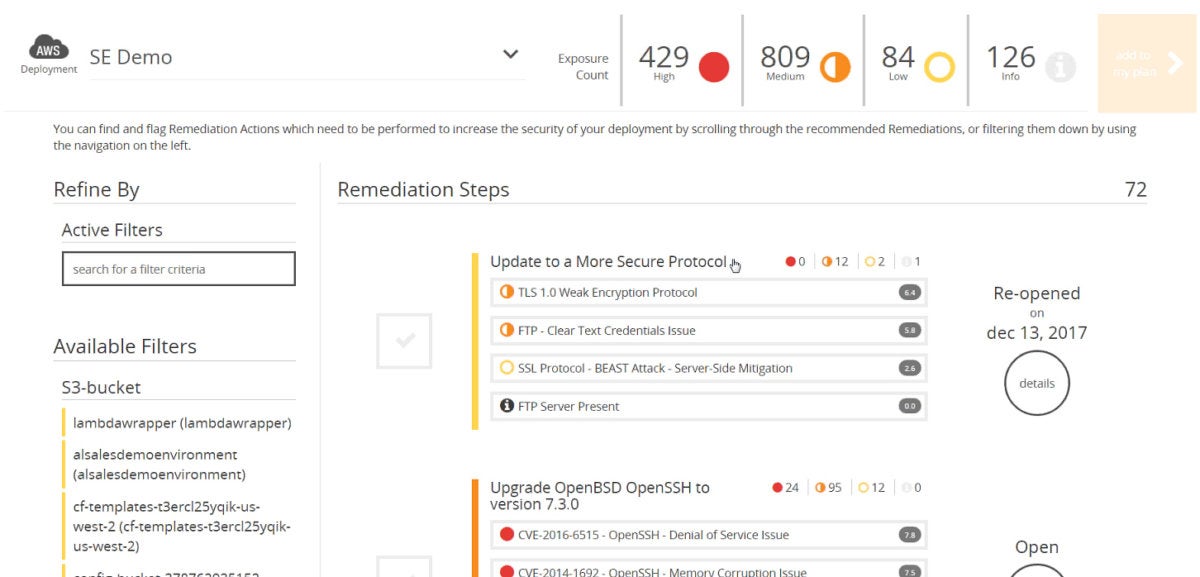
Once deployed, Cloud Defender gets to work on reducing the attack footprint within the cloud. It does this by targeting vulnerabilities, which it collects and presents to local IT teams. It can find all manner of potential problems, such as weak encryption on logins or protecting critical assets, the existence of certain communications protocols such as FTP where they are not needed, or servers and applications that don’t have the latest patches.
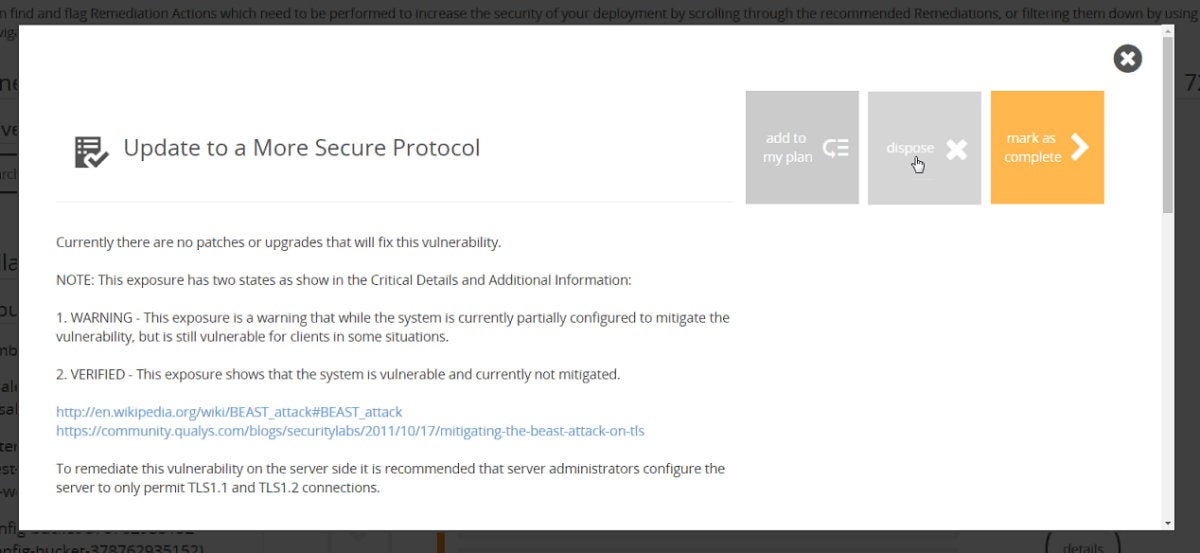
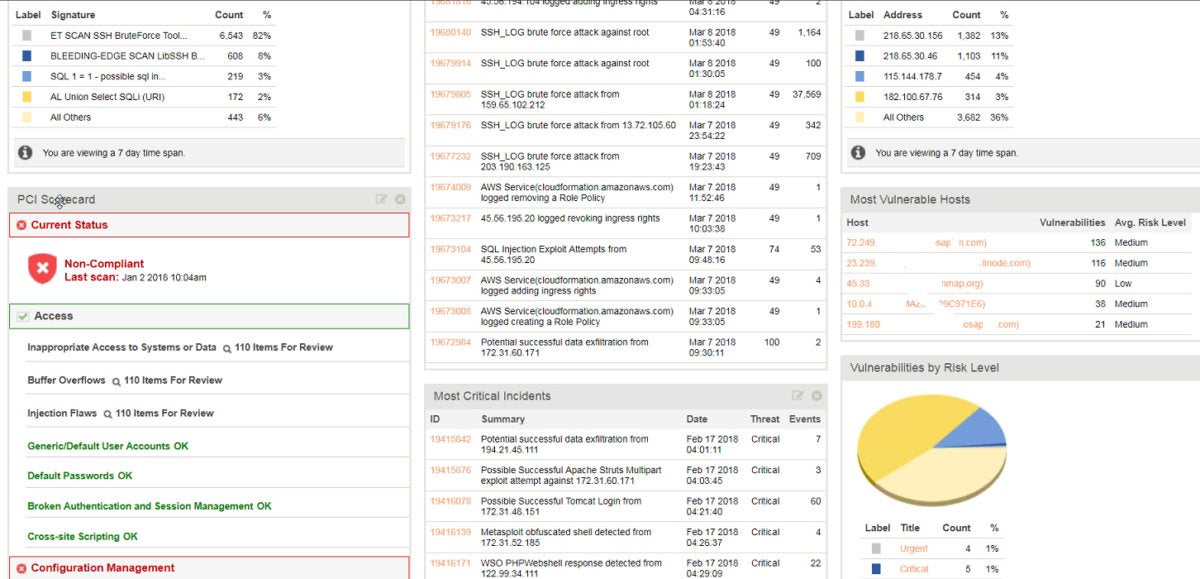
These issues are presented into the Cloud Defender console, which looks very much like a traditional security information and event management (SIEM) console. The data integrates easily into any existing tracking or ticketing system. For example, in our testing, we were able to add vulnerability issues to our existing work plan, which dropped it into a ticketing system for tracking. Once the issue was resolved, the ticketing system reported this data back to Cloud Defender, which verified that the vulnerability had been eliminated. We could also flag issues as unimportant or even as a false positive, which removes it from further tracking.
Once the vulnerabilities are eliminated, or even while this process is still ongoing, Cloud Defender can begin tracking security issues affecting the protected cloud deployment. One smart thing that organizations deploying Cloud Defender will want to do is to add the agent protocol to their cloud’s golden image. That way, every new service or server spun up within the cloud will have the Cloud Defender agent in place, ready to report on critical issues right from the start.
 John Breeden II/IDG
John Breeden II/IDG
You can use Cloud Defender exactly like this, as a sort of cloud-based SIEM, and get a lot of useful information from it about cloud security and vulnerability issues. And if there is a large cybersecurity team in place locally with a lot of cloud experience, that is probably enough. However, most organizations could probably do with a little help, and Cloud Defender offers this through its ActiveWatch program.
In truth, the ActiveWatch program for Cloud Defender is probably a good idea even if an organization has a big IT team, as it adds another set of eyes that can concentrate on cloud assets. Part of that service involves having analysts at Alert Logic monitor cloud activity. In our testing, they could see things like anomalies in traffic at Layer 7, which is one of the most attacked these days. Analysts could then dig down into the packet level and find evidence of ongoing attacks and exploit attempts, even those that were crossing over into on-prem assets.
It’s worth noting that in addition to having the Cloud Defender teams do this kind of threat hunting-like investigation, that the same tools are also available for local teams. It’s just that most IT teams don’t have the time or resources to watch everything, especially with large cloud deployments.
When a critical threat was identified during our testing, the Cloud Defender teams were able to reach out to the local IT team using a console, e-mail, the ticketing system or even by phone. They were able to explain the exact nature of the threat, backed with evidence that encompassed the entire attack structure including how many clients were compromised. The teams at Cloud Defender don’t actually remediate problems, but can walk local staff through the process and make recommendations. Once fixed, Cloud Defender can confirm that the threat has been eliminated, and that proper protections are in place to prevent it from returning.
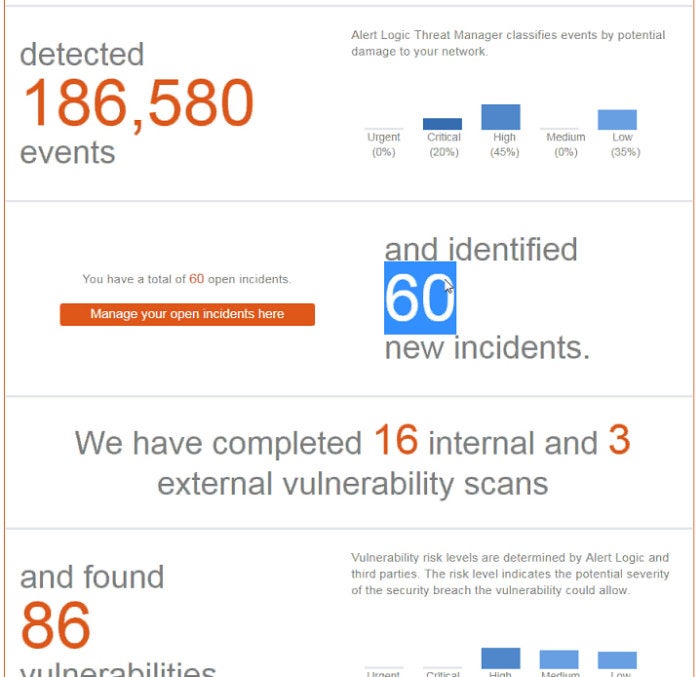
As an additional service, Cloud Defender can generate highly detailed reports showing everything that has been found by the platform since it was installed.
It can also create a user-friendly report for management that shows in plain English how many events were detected and remediated, the number of vulnerabilities that were fixed and other data to help justify the return on investment in the program.
The cloud is nebulous by nature, and attackers are exploiting this with new techniques and attacks designed to sneak into critical cloud-based infrastructures. Having a team of experts watching over a cloud deployment, along with a set of tools to empower local staff to defend their own clouds, is a critical component to a good cybersecurity plan. Cloud Defender accomplishes this in an elegant way that can be up and running almost immediately.
Comments