Top 10 Most Dangerous Financial Malware
1. Zbot/Zeus
Zeus, also known as Zbot, is a notorious Trojan which infects Windows users and tries to retrieve confidential information from the infected computers. Once it is installed, it also tries to download configuration files and updates from the Internet. The Zeus files are created and customized using a Trojan-building toolkit, which is available online for cybercriminals.
Zeus has been created to steal private data from the infected systems, such as system information, passwords, banking credentials or other financial details and it can be customized to gather banking details in specific countries and by using various methods. Using the retrieved information, cybercriminals log into banking accounts and make unauthorized money transfers through a complex network of computers.
Zbot/Zeus is based on the client-server model and requires a Command and Control serverto send and receive information across the network. The single Command and Control server is considered to be the weak point in the malware architecture and it is the target of law enforcement agencies when dealing with Zeus.
To counter this weak point, the latest variant of Zeus/Zbot have included a DGA (domain generation algorithm), which makes the Command and Control servers resistant to takedown attempts. The DGA generates a list of domain names to which the bots try to connect in case the Command and Control server cannot be reached.
Zeus/Zbot, known by many names including PRG and Infostealer, has already infected as many as 3.6 million systems in the United States. In 2009, security analysts found that the Zeus spread on more than 70,000 accounts of banks and businesses including NASA and the Bank of America.
For more information about the Zbot/Zeus malware, check out this article.
2. Zeus Gameover (P2P) (Zeus family)
Zeus Gameover is a variant of the Zeus family – the infamous family of financial stealing malware – which relies upon a peer-to-peer botnet infrastructure.
The network configuration removes the need for a centralized Command and Control server, including a DGA (Domain Generation Algorithm) which produces new domains in case the peers cannot be reached. The generated peers in the botnet can act as independent Command and Control servers and are able to download commands or configuration files between them, finally sending the stolen data to the malicious servers.
Zeus Gameover is used by cybercriminals to collect financial information, targeting various user data from credentials, credit card numbers and passwords to any other private information which might prove useful in retrieving a victim’s banking information. GameOver Zeus is estimated to have infected 1 million users around the world.
For more info about the Zeus P2P Gameover malware, read this article.
3. SpyEye (Zeus family)
SpyEye is a data-stealing malware (similar to Zeus) created to steal money from online bank accounts. This malicious software is capable of stealing bank account credentials, social security numbers and financial information that could be used to empty bank accounts.
This banking Trojan contains a keylogger that tries to retrieve login credentials for online bank account. The attack toolkit is popular among cybercriminals because it can be customized to attack specific institutions or target certain financial data.
SpyEye is able to start a financial transaction as soon as a targeted user initiates an online operation from his bank account.
For more information about the SpyEye malware, check this article.
4. Ice IX (Zeus family)
Ice IX is a modified variant of Zeus, the infamous banking Trojan, one of the most sophisticated pieces of financial malware out there.
This modified variant is used by cybercriminals with the same malicious purpose of stealing personal and financial information, such as credentials or passwords for the e-mail or the online bank accounts.
Like Zeus, Ice IX can control the displayed content in a browser used for online banking websites. The injected web forms are used to extract banking credentials and other private security information.
Ice IX, the modified version of Zeus, improved a few Zeus capabilities. The most important one is a defense mechanism to evade tracker sites, which monitor at present most Command and Control servers controlled by Zeus.
To find more information about the Ice IX malware, this article is a good resource.
5. Citadel (Zeus family)
Citadel appeared after the source code of the infamous Zeus leaked in 2011. Due to its open source character, the software code has been reviewed and improved by IT criminals for various malware attacks.
For cybercriminals, it is an advanced toolkit which they can use to trick users into revealing confidential information and steal banking credentials. The stolen credentials are then used by cybercriminals into accessing online accounts and running fraudulent transactions.
For more information about the Citadel malware, see this article. And, if you want, you can also read about its successor, Atmos, which emerged in the first half of 2016.
6. Carberp (Zeus family)
Carberp is a Trojan designed to give attackers the ability to steal private information from online banking platforms accessed by the infected PCs.
This Trojan’s behavior is similar to the other financial malware in the Zeus family and displays stealth abilities from antimalware applications. Carberp is able to steal sensitive data from infected machines and download new data from command-and-control servers.
This Trojan is one of the most widely spread financial stealing malware in Russia. Primarily targeting banking systems and companies which perform a high number of financial transactions, Carberp is not only injecting a code into web pages, but it also tries to exploit several vulnerabilities in the target system so as to escalate to administrative privileges.
Distributed through the typical methods of using malicious e-mail attachments, drive-by downloads or by clicking on a deceptive pop-up window, what is different at this financial malware is the high number of legitimate web resources used to collect information and potentially make fraudulent transactions. It is indicated that cybercriminals have deployed botnets on over 25,000 infected machines.
To learn more about the Carperb malware, this is a good resource.
7. Bugat (Zeus family)
Bugat is another banking Trojan, with similar capabilities to Zeus – the notorious data-stealing Trojan – which is used by IT criminals to steal financial credentials.
Bugat targets an infected user’s browsing activity and harvests information during online banking sessions. It can upload files from an infected computer, download and execute a list of running processes or steal FTP credentials.
Bugat communicates with a command and control server from where it receives instructions and updates to the list of financial websites it targets.
The collected information is sent to the cybercriminal’s remote server.
Cybercriminals spreads the malware mostly by inserting malicious links in the e-mails they send to the targeted users. When a user clicks a malicious link, he is directed to a dangerous website where the Bugat executable downloads on the system.
For more information about the Bugat malware, check out this article.
8. Shylock (Zeus family)
Shylock is a banking malware, designed to retrieve user’s banking credentials for fraudulent purposes.
As soon as it is installed, Shylock communicates with the remote Command and Control servers controlled by the cybercriminals, sending and receiving data to and from the infected PCs.
Similar to Zeus Gameover, this malware makes use of a (DGA) Domain generation algorithm which is used to generate a number of domain names that can be used receive commands between the malicious servers and the infected systems.
The Trojan is delivered mostly through drive-by downloads on compromised websites and via malvertising, where malicious code is inserted in adverts that are then placed on legitimate websites.
Another popular method of spreading this financial malware is by inserting malicious JavaScript into a web page. This technique produces a pop-up which pushes the user to download a plugin, apparently necessary for the media display on the website.
For more information about the Shylock malware, you can use this resource.
9. Torpig (Zeus family)
Torpig is a sophisticated type of malware program designed to harvest sensitive information, such as bank account and credit card information from its victims.
The Torpig botnet – the network of compromised PCs – which are under the control of cybercriminals are the main means for sending spam e-mails or stealing private information or credentials for the online bank accounts. Torpig also uses a DGA (domain generation algorithm) to generate a list of domains names and locate the Command and Control servers used by hackers.
Users are typically infected through drive-by downloads; a web page on a legitimate website is modified to ask the user for JavaScript code from a web location controlled by the IT criminals. The infected computers run phishing attacks to obtain sensitive data from its victims.
For more information about the Torpig malware, you can read this article.
10. CryptoLocker
This malware encrypts your data and displays a message which states that your private information can be decrypted for a sum of money in a limited period of time. Though CryptoLocker can be removed by various security solutions, there isn’t any way yet to decrypt the locked files.
CryptoLocker is one of the nastiest pieces of malware ever created. It’s not just because it takes money from you or because it can access your private data, but once it manages to encrypt your information, there is no way for you to decrypt those files. This ransomware is so dangerous because the affected users have their private information disclosed (and taken advantage from) and they also lose the files without having any chance of recovering them.
CryptoLocker is a ransomware Trojan which can infect your system in different ways, but usually this happens through the means of an apparently legitimate e-mail attachment, from a well-known company or institution. Because it spreads through e-mail attachments, this ransomware is known to target companies and institutions through phishing attacks.
HOW DO I STAY SAFE FROM CRYPTOLOCKER?
To stay safe from CryptoLocker, follow these steps:
- Install a specialized security solution, such as Heimdal PRO.
- Be careful at the e-mails you receive and don’t download or run e-mail attachments from unknown e-mail senders. Also, don’t click the links in these types of e-mails.
- Back up your important documents and files. Create backup copies of your data in multiple locations.
- Keep your software up to date, using the latest security patches available.
And there’s more advice in our protection guide against ransomware.
HOW CAN HEIMDAL PROTECT ME FROM CRYPTOLOCKER?
Heimdal blocks malicious websites which distribute CryptoLocker by making sure that users do not establish untrusted connections. Heimdal can shield a PC from an attacker’s domain and it can prevent CryptoLocker from downloading its encryption keys, even if a PC has already been infected.
An example on how Heimdal protects users from financially exploiting malware, such as Cryptolocker, can be seen below.
For more information about Cryptolocker, read this article.
What is the typical spreading method for financial malware?
Most dangerous pieces of financial malware are usually distributed through:
The user receives an e-mail message from a well-known organization with some false banking information attached or with a link included in the e-mail. The system becomes infected when the user clicks the link or downloads the file attached to the e-mail, usually disguised as an important invoice or job offer.
- drive-by downloads
A drive-by download occurs when the user visits a website or clicks a deceptive pop-up window.
A diagram on the typical spreading method of financial malware can be seen below:
What does a typical financial attack look like?
We will start from the point where a normal machine is already infected by a credentials stealing malware. As we mentioned before, the machine may have become infected through:
- an e-mail attachment (or an e-mail link)
- a drive-by download (which occurs when visiting a website)
- a deceptive pop-up window.
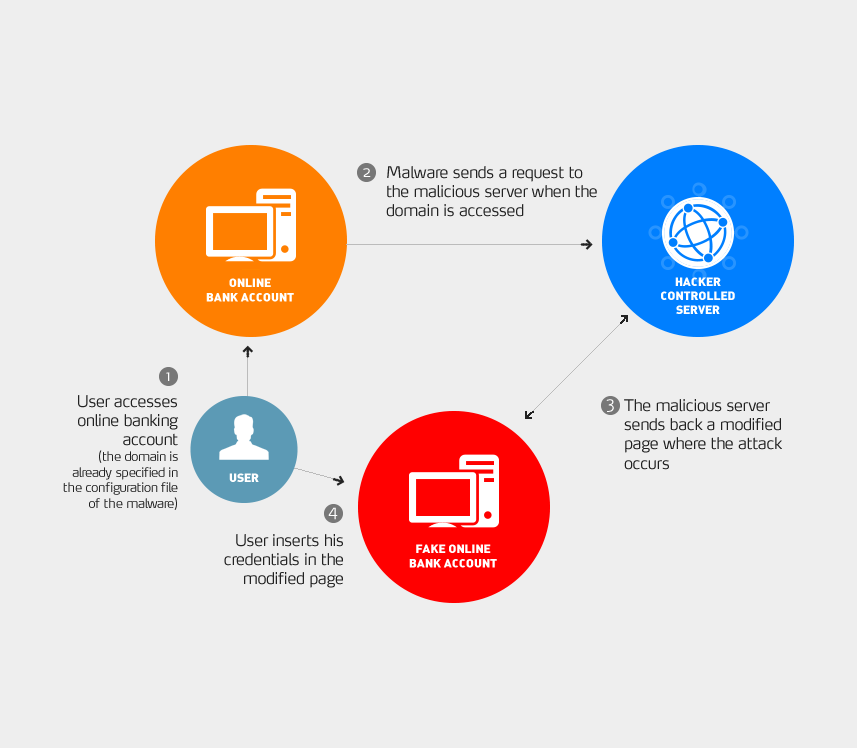
The following steps usually occur in a typical financial attack:
- The user accesses his online banking account. The domain is specified in the configuration file downloaded by the malware from the malicious servers controlled by the hackers.
- The malware sends a request to the malicious servers controlled by cybercriminals and lets them know the user is trying to access the domain specified in the configuration file.
- The malicious server specifies a page on the online banking account – usually the login page – where the attack should occur.
- When the user accesses the specified page, the malware sends a request to the malicious server which sends back a modified page into the user’s browser. The modified page should trick the user into believing he enters his credentials in the normal page of the online banking account.
- The modified page (the login page in our case) asks for user’s sensitive information, such as credentials for online banking website or the credit card number
Here’s a diagram for a typical financial malware attack:
This is just a typical phishing attack used by IT criminals, but their means and tools vary from stealing the credentials through the classical method of using a keylogger software, to withdrawing money directly from the online banking account


Comments